In the Web3 world, where innovations are experienced every day, some problems arise along with innovations. In this article, we’ll cover the Notebook Labs project and what problems it solves.
Problem
Accuntable identity is something we all have in our daily life. For example, when you get a traffic ticket or get involved in any crime, the responsible institutions will know what we look like or where we live, etc. knows. Thus, they can arrest us. KYC is a must against law enforcement in financial services in Web2 technology. But the downside is privacy. While users can remain anonymous with Web3, the disadvantage is insecurity and the inability to call someone to account.
DeFi has become a hub for financial crimes. Opensea estimates that almost 80% of NFT projects are fraudulent. This lack of trust in Web3 has been felt very strongly, especially recently. At this point, the Notebook, a protocol that provides Sybil-resistant login, identity information collection, and accountability and trust while maintaining anonymity and privacy, is a project that has been implemented to solve all problems.
Secure Web3
Believing in decentralization and privacy as a team, Notebook has made it its mission to secure Web3 for its universalization. Notebook provides its users to protect their anonymity by shredding their identities with the following five features. These are:
- Users can prove that they are human with any fragmented identity.
- It is impossible to link these identities together (Unless the user’s secret key is leaked.).
- It is impossible for any third party or adversary to link a fragmented identity to the user’s real-world identity.
- Identity information can be aggregated between identities
- Each person receives a single fragmented set of identities
Overview
Notebook Labs allows people to prove both on-chain and off-chain identity data and collect reputation points across their fragmented identities. A single SSI depth has 36 trees for all users. Each reputation point is a 256-depth tree, in which leaves are allocated to users through a hash function.
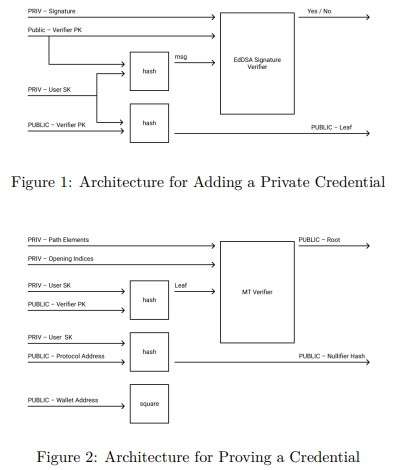
The Self-Sovereign identity works through a verified identity information system. Users will receive a credential that has been verified and validated by the third-party organization. (The schematic explanation of this is summarized in Image 1.)
How Can Someone Prove Their Credentials?
Any protocol can require any user to prove ownership over the Notebook. For example, they may want to check whether the user is a bot or not. The proof of this proof is shown in Image 2. The proof of opening is given by the system, as a secret entry that prevents the protocol or anyone from finding out when the credentials were used or by which other wallets.
How Does KYC Verification Work?
Notebook Labs offers another side called ‘compliance organization’. That is a method of linking users’ private personal information to wallet addresses to fulfil the KYC regulations. This entity cannot link a user’s PII to KYC credentials and must cooperate with the KYC validator to establish this connection. The role of this entity is to decide when the link between a user’s wallet address and PII will emerge, based on regulators’ needs. Initially, the party who will perform this role will be the Notebook Labs team, but in the future, this process will also be removed from the team.
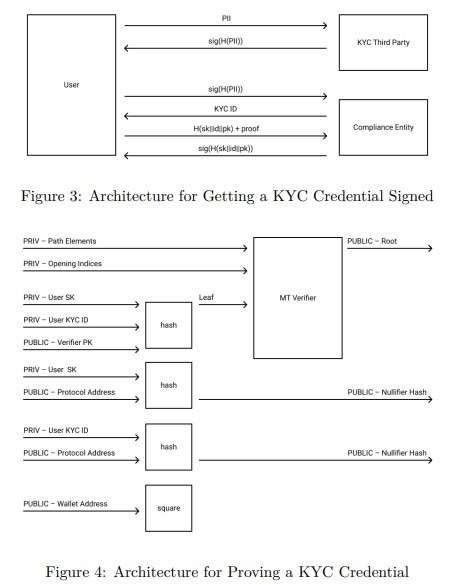
The general scheme for signing KYC credentials is summarized in Image 3. Both the KYC validator and the compliance entity have ECDSA keys. The KYC third party knows the hash between the user’s PII and their PII. The compliance organization knows the link between the hash PII and wallet addresses using KYC credentials. It does this by giving the user a unique ‘KYC ID’ when generating their KYC credentials.
Each time a user uses KYC credentials, they publish a hash of the protocol address of the KYC ID. While viewers can’t learn anything from this hash, compatibility can find the asset in O(n) time. The “n” specified here is the number of KYC IDs.
Summary
With the lack of trust in Web3 felt very strongly lately, Notebook Labs is a protocol for Sybil resistant login, credential collection and maintaining anonymity and privacy while at the same time providing accountability and trust and is a project implemented to solve all problems. The Notebook allows users to maintain their anonymity by shredding their identities. Notebook Labs offers another side called ‘compliance organization’. That is a method of linking users’ private personal information to wallet addresses to fulfil the KYC regulations. Although the project team will see this process initially, it will be completely removed from the team in the future.
Visit Our Other Blogs: All News















Leave a comment