Breaking Crypto News – Unveiling the Dark Side: Trends in AI-Enabled Crypto Crime
Breaking Crypto News – “The State of AI-Enabled Crypto Crime: Emerging Typologies and Trends to Look Out For” is a thorough analysis that was just produced by the blockchain analytics startup Elliptic. The worrying development of artificial intelligence (AI) to enable several cryptocurrency crimes is highlighted in this report. Five basic typologies of using AI in crypto crimes are identified in the Elliptic report.
1. Deepfake
The first, and arguably most well-known, is the application of deepfakes created by AI. Scammers frequently exploit fictitious photos or videos of well-known people to produce convincing fakes. For instance, to advertise phony investment schemes, scammers have created deepfakes of celebrities such as Elon Musk and the former prime minister of Singapore, Lee Hsien Loong.
2. Scam Tokens
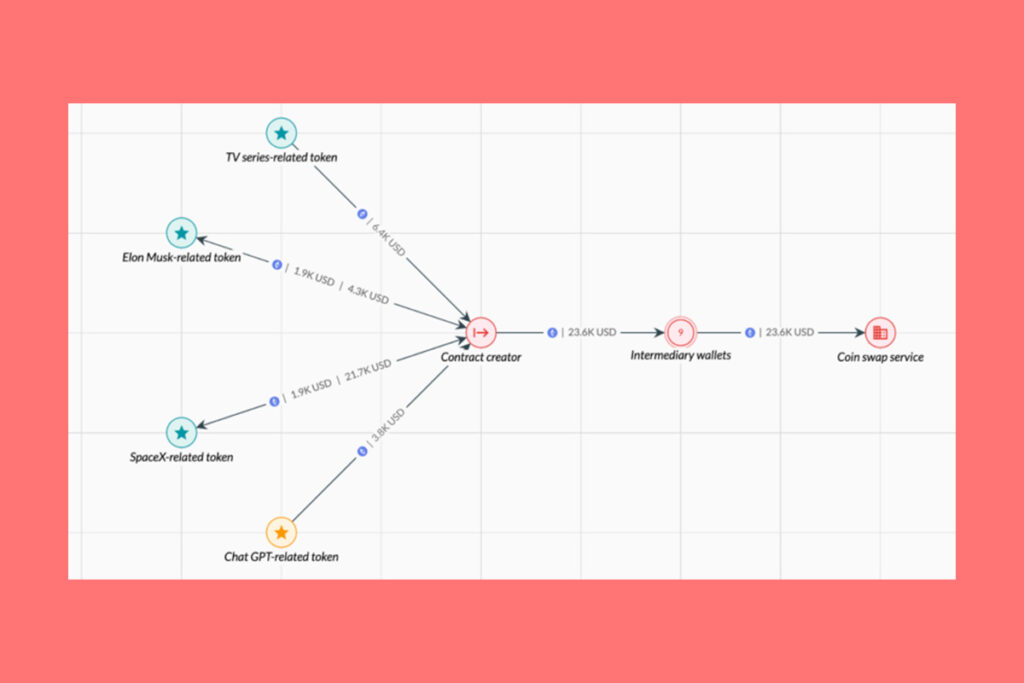
The development of scam tokens is another common crime that AI facilitates. It is comparatively simple to establish a new token on many blockchains, which scammers take advantage of to build anticipation and artificially raise values prior to carrying out a “rug-pull” or a “pump-and-dump” operation. AI-related tokens, like “GPT,” have proven to be especially appealing targets. Numerous exit scams utilizing these tokens were discovered by Elliptic’s analysis, underscoring the importance of exercising caution when investing in tokens.
3. AI Tools (like ChatGPT, HackedGPT and WormGPT)
To help with their illegal activities, cybercriminals have also taken advantage of broad language models such as ChatGPT. AI technologies have the ability to create new code or audit already-written code, which can be abused to find and take advantage of security holes. However, the appearance of immoral AI tools on dark web forums, such as HackedGPT and WormGPT, which provide services for hacking, malware generation, and phishing, is a serious threat.
4. Automation of Scam Deployment
The automation of scam deployment is another area that AI is influencing. In certain fraud operations, fictitious giveaway sites, airdrops, or investments are created and extensively publicized via messaging apps and social media. These sites are abandoned after they are made public, and new sites and marketing are used to restart the process. This cyclical process is being streamlined by AI to make it more effective and difficult to track down.
5. Identity Theft and False Documents
The dark web has long been associated with identity theft and the fabrication of papers. AI is currently being used by several services to scale their operations. For example, one document-rendering service claimed to be able to create high-quality forged passports and IDs using AI.
Elliptic has identified a crypto address used for payments to this service, which has received enough payments to generate just under 5,000 fake documents in the space of a month,
the firm
FAQ
How Artificial Intelligence Affects Crypto Crimes?
Although AI has revolutionized numerous industries, its abuse in the cryptocurrency space is starting to raise serious concerns. Hackers can use AI to discover and exploit new vulnerabilities.
What is Deepfake?
Initially, artificial material that has been digitally altered to accurately mimic the appearance of one person was referred to as a “deepfake.”
What is a Scam Token?
A mysterious token that looks to be worth hundreds of dollars suddenly shows up in your wallet. A smart contract is triggered if you sell it. This gives the con artist access to your private keys and authentic cryptocurrency tokens.
How are AI Tools Used in Hacking?
Hackers increase the speed, scalability, and sophistication of assaults by automating them with AI algorithms.
Can Someone Steal Your Identity from Crypto?
It is perfectly possible to buy someone’s whole name, social security number, and digital ID on the darknet. Know Your Customer (KYC) checks are one way that this can be prevented. Essentially, these checks entail separating actual identities from identity theft.
For more up-to-date crypto news, you can follow Crypto Data Space.















Leave a comment